
December 12, 2023

December 12, 2023








March 21, 2023

February 27, 2023

February 22, 2023

February 17, 2023

January 31, 2023
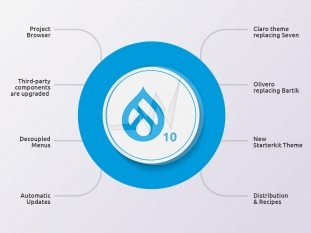

January 09, 2023
Join us to stay updated with our latest blog updates, marketing tips, service tips, trends, news and announcements!